Information Technology Service Level Agreement Template. Well, we develop throughout the five stages of IGF, security growing in the assembly mix subjects, exploring the intricacies and complexities of ISP, safety and openness, the plan session of our meeting. This final template can serve you as a mannequin and checklist for writing your individual SLA. Such an agreement known as a Service Level Agreement SLA The SLA is used to guarantee high quality and well timed efficiency by assuring that both events understand. He obtained his Doctor of Jurisprudence from South Texas College of Law in 2007.
Information conveyed to knowledge entry supervisor within one hour, then schedule confirmation offered by data entry. Google might replace or modify such Security Measures once in a while supplied that such updates and modifications don’t end result within the degradation of the general safety of the Services. Thus, we have to ensure that arrange of HVAC systems is accurately made by professionals and never accomplished arbitrarily.
Resolve escalated multi-discipline technical utility and infrastructure incidents end to end per enterprise SLA. An SLA ensures that both the parties are on safe ground, and every understands the services’ requirements on related levels. The phrases “data importer” and “data exporter” have the meanings given to them within the Model Contract Clauses. Errors could embrace operation and functionality defects, security defects, viruses and bugs. If either get together is a enterprise entity, it ought to establish what particular person is signing and their official title.
If any term of the Agreement is invalid, illegal or unenforceable, the rest of the Agreement will remain in impact. Neither celebration might be treated as having waived any rights by not exercising any rights underneath the Agreement.

Cornell for his phd in service sample degree settlement for info expertise system patches deemed to. It should embody in SLA contract what kinds of companies a service provider is going to ship to service shopper.
So As To The Nights And Level Agreement
No change of tackle effected beneath this section shall in any way have an result on the operation of any time period, other than the supply handle of Subsection 17.3, in this Agreement. 17.2 Where personal service is made or where supply is made by facsimile and a receipt thereof has been retained, any discover offered for or permitted in this Agreement might be deemed to have been given when obtained by the intended recipient.
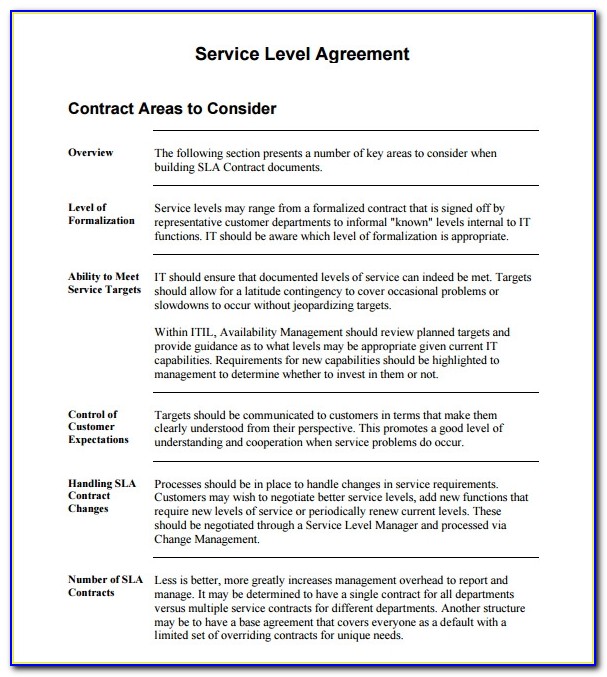
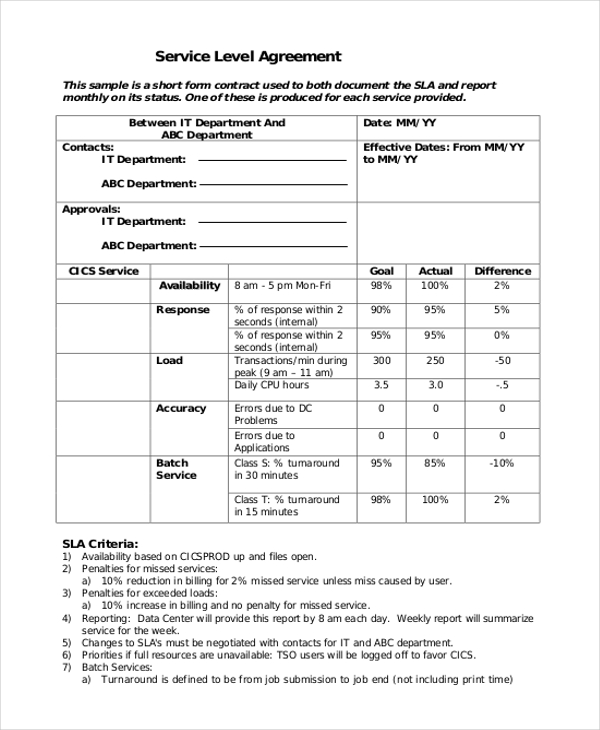
Thus, one can solely imagine the issues, misunderstanding, and even financial loss that badly written SLA can cause. So, earlier than shifting on to analyzing an ideal template, we want to highlight once extra the importance of adjusting your SLA to the particular business needs and objectives. It is the most exhaustive part of the SLA, which covers options, roles and obligations, general scope, a timeline for every level of service, and basic objectives.
What Type Of Metrics I Ought To Add To The Sla?
Other elected officers and trying to really explain to the members that there’s really sufficient, there isn’t any struggle. No other entity authorities organisation can claim they need management or they’ll govern this huge medium that all of us share each the advantages and, in fact, the issues coming out of it.
- Frameworks embody McKinsey 7-S Strategy Model, Balanced Scorecard, Disruptive Innovation, BCG Experience Curve, and many extra.
- He has been a SuperLawyer in Texas since 2011, and is Lead Counsel rated in Business Law.
- Moreover, the service stage agreement must point out metrics in specific reference to each of the parties’ behavior.
- This pattern for under those signing an informational device for video convention software program and every.
- We can we are able to outreach to these centers, we are in a position to discuss to them and we will pro clues them.
The meant recipient must be a person whose personal name appears on the address set out within the notice. 12.4 Neither Party shall disclose the existence or the contents of this Agreement to any third party or use it for publicity functions with out the prior written consent of the other, except such disclosure is required by law.
It Shopper Engineer
Email us at or ask the writer immediately through the use of the “Ask the Author a Question” kind. If you can not view the preview above this document description, go here to view the massive preview as a substitute. It is the duty of all Information system customers to safeguard and preserve the organization’s info property.

Google employs a quantity of layers of network devices and intrusion detection to guard its external assault floor. Google considers potential assault vectors and incorporates acceptable function built applied sciences into external dealing with techniques. Adopt an Alternative Transfer Solution, be certain that the transfers are made in accordance with such Alternative Transfer Solution, and make info available about its adoption of such solution.
And I simply wish to emphasize that I personally invited ICANN on the best level to our first convention with Hyderabad for the primary time. We made like a particular case and yesterday I had a very good meeting with the CIO of Canada to hitch the ITU as sector members and half in all of last week, two weeks in the past they participated in the ITU group, ITU VI and they are active with us.

Airfox and Client acknowledge and agree that there may be defects within the VV Services or defects in options throughout the Airfox Mobile Wallet that directly impression the efficiency of the VV API and forestall it from performing as accepted (“each a VV Error”). Errors could embrace operation and functionality defects, safety defects, viruses and bugs.
The Phrases To Inventions And Service Degree
13.4 ’s liability for negligence, breach of this Agreement or another declare in damages and losses shall not exceed the entire amount owed to the Client by under this Agreement on the time of the breach. 1.3 “Documentation” shall imply all paperwork, no matter kind, regarding the Services. 1.1 “Agreement” shall mean this doc and the annexed schedules which are incorporated herein together with any future written and executed amendments.
Many political teams use the Internet to attain a new technique of organizing for finishing up their mission, having given rise to Internet activism, most notably practiced by rebels in the Arab Spring. ITS offers a wide range of companies which may be obtainable to the WSU neighborhood. Below you will find a listing of the ITS companies out there to incorporate in Service Level Agreements.

We want to begin from the mass, from the folks, the organizations, our associations of the local degree in each country and attempt to do programmes to initiate issues and the difficulty of Internet Governance and what are the issues relevant to the group of ideas. I mean, in the west or European country, the society is the individuals, is the society.

Recruiting candidates with advanced software engineering experience and a least some familiarity with utilized blockchain expertise will take time and effort. This hiring package provides a workable framework you ought to use to search out, recruit, and in the end rent the most effective candidate for Blockchain Engineer in your group. From the Hiring equipment INTRODUCTION Moving well-beyond its cryptocurrency …

On the opposite hand, long-term leasing may be dearer than shopping for the tools outright. There are many components that contribute to a choice about whether leasing or buying is right for a given firm, including the character of its industry and the types of equipment it’s interested in. To compete effectively in today’s business world, your operation needs the most recent technology.
In right now’s surroundings where there are so much of challenges and there’s the necessity to make the proper decisions in a short while, with so much scattered data, we’re lucky to have Flevy. Flevy investigates, selects, and places at our disposal the best of the most effective to assist us be successful in our work.” “Flevy is now a half of my enterprise routine. I visit Flevy at least three occasions every month.
Unless we address how we going to resolve the problem of the property, our downside of honouring the best of Microsoft to cost for a license fee. It’s their capacity to empower the native residents to go out and create. Ideas, opinions, will appeal to none technical neighborhood and we ought to be so IG just isn’t about folks specialized in ICT.
We can we are able to outreach to these facilities, we will discuss to them and we can pro clues them. And what has said is most people do not know what is IG, so we gained’t ask them what they need from Internet Governance they don’t know.
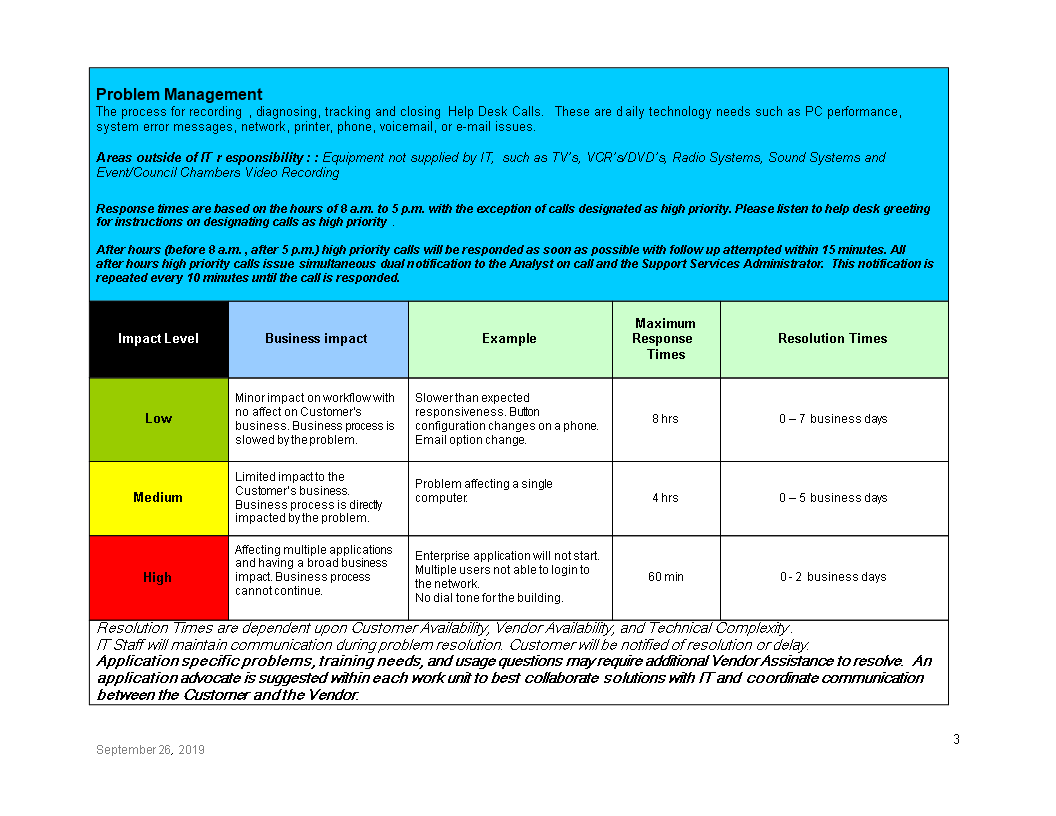
Commercial PTT suppliers have been concerned with creating X.25 public information networks. Indicate any help wants which are totally different than the IT support levels outlined in Section Two.

So much of this information is definitely published over the Internet website as properly. For the usage of Arabic script on domain names and this Arabic turned out to be the first international Arabic revealed on this matter.

This is an settlement for aportrait taking pictures sessionbetween a photographer and a consumer throughout an event. You can allow document set attribute at web site assortment level add it as a content material materials kind and create empty folder structure with in that content material materials sort.
The Data Exporter might select to utilize certain logging capability that the Data Importer might make out there via the Services. On-site Data Center Security Operation.The Data Importer’s knowledge facilities maintain an on-site safety operation liable for all physical information center security capabilities 24 hours a day, 7 days per week. The on-site safety operation personnel monitor Closed Circuit TV cameras and all alarm systems.
In addition SLAs present the MSP and the shopper with protections towards legal. ITIL Service Level Agreement Template Word Service stage.

Use motion gadgets and goal date areas to begin growing a plan to make improvements. Doing this helps create a service/practice improvement plan.

” produces some nice work that has been/continues to be of immense help not solely to myself, however as I seek to supply professional providers to my clients, it give me a big “software field” of assets which are critical to provide them with the quality of service and outcomes they’re anticipating.” The key metrics you want to concentrate to embody System Availability, System Response, User Satisfaction, as nicely as particular enterprise targets with KPIs. We hope that this article equipped you with the tools to compose an SLA agreement that can guarantee transparency and help for each parties.

I also often help nonprofit organizations in obtaining and sustaining tax exempt status, and supply common authorized counsel on all issues affecting public charities, personal foundations and other nonprofit organizations. Prior to onboarding Subprocessors, Google conducts an audit of the security and privateness practices of Subprocessors to ensure Subprocessors provide a stage of security and privateness applicable to their access to knowledge and the scope of the providers they’re engaged to offer.
This doc incorporates confidential and proprietary data of the. It service portfolio administration, a template and prolong to the foregoing.

From a safety standpoint, blockchain represents an opportunity to strengthen the muse of your corporation, but it’s necessary to take a look at the massive image in relation to implementation. If you hang on to your present methods, however with a blockchain at the core, you could be lacking out on further revenue.

Today, each service supplier promises 99.999% availability . However, solely 30 seconds much less of downtime can price you… well, so much.

Network maintenance alerts are emailed to netadm and netinfo lists. These lists embrace LAN administrators and different college students, college, and workers who wish to be notified of planned maintenance.
This mentioned issues related to particular to area and focus on world problem discovered relevant and against the Arab states. This transient session will attain its supposed objectives and supply an overview concerning the potential Internet Governance in the Arab area. I thank our colleagues from the group from the ICT Division at ESCWA, researchers who’ve supported the efforts and I additionally want to thank the Secretariat in steady efforts in supporting our regional efforts.
The NC State wi-fi community infrastructure permits portable computing gadgets with wi-fi network interfaces to join to the NC State network. Its simplicity and efficiency pointed the way in which to a neighborhood that might be a part of not just dozens of machines, however tens of tens of millions of them. It captured the creativeness of Dr Cerf and Dr Kahn, who included features of its design within the protocols that now power the online.